On Detecting Malicious Code Injection By Monitoring Multi-level Container Activites
Computer Security, Cloud Security
Supervisor:
Prof. Md Shohrab Hossain
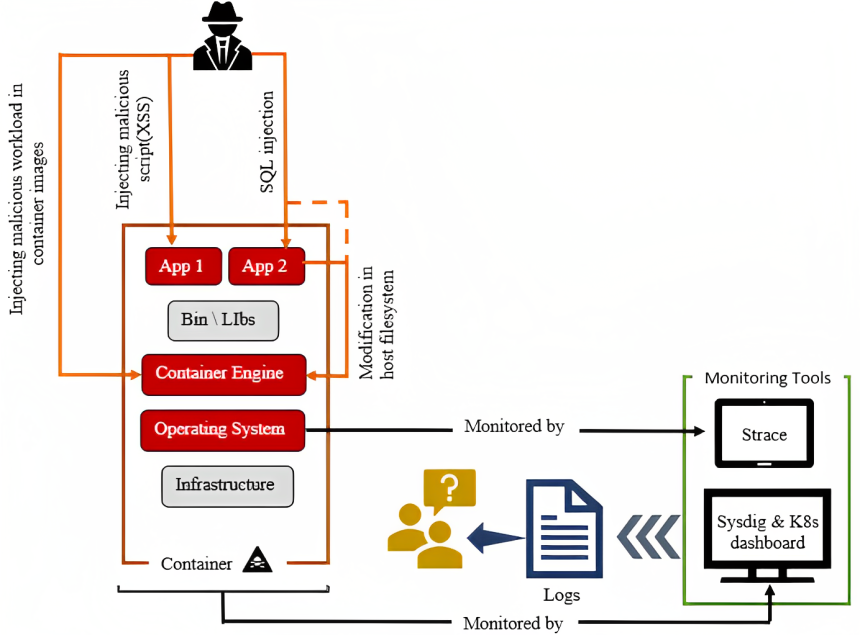
In recent years, cloud-native applications have been widely hosted and managed in containerized environments due to their unique
benefits, such as being lightweight, portable, and cost-efficient. Their growing popularity makes them a common subject of cyberthreats,
as evidenced by recent attacks. Many of those attacks take place due to malicious code injection to breach systems and steal sensitive
data from a containerized environment. However, existing solutions fail to classify malicious code injection attacks that impact
multiple levels (e.g., application and orchestrator). In this paper, we fill in this gap and propose a multi-level monitoring-based
approach where we monitor container activities at both the system call level and the container orchestrator (e.g., Kubernetes) level.
Specifically, our approach can distinguish between the expected and unexpected behavior of a container from various system call
characteristics (e.g., sequence, frequency, etc.) along with the activities through event logs at the orchestrator level to detect
malicious code injection attacks. We implement our approach for Kubernetes, a major container orchestrator, and evaluate it against
various attack paths outlined by the Cloud Native Computing Foundation (CNCF), an open-source foundation for cloud native computing.
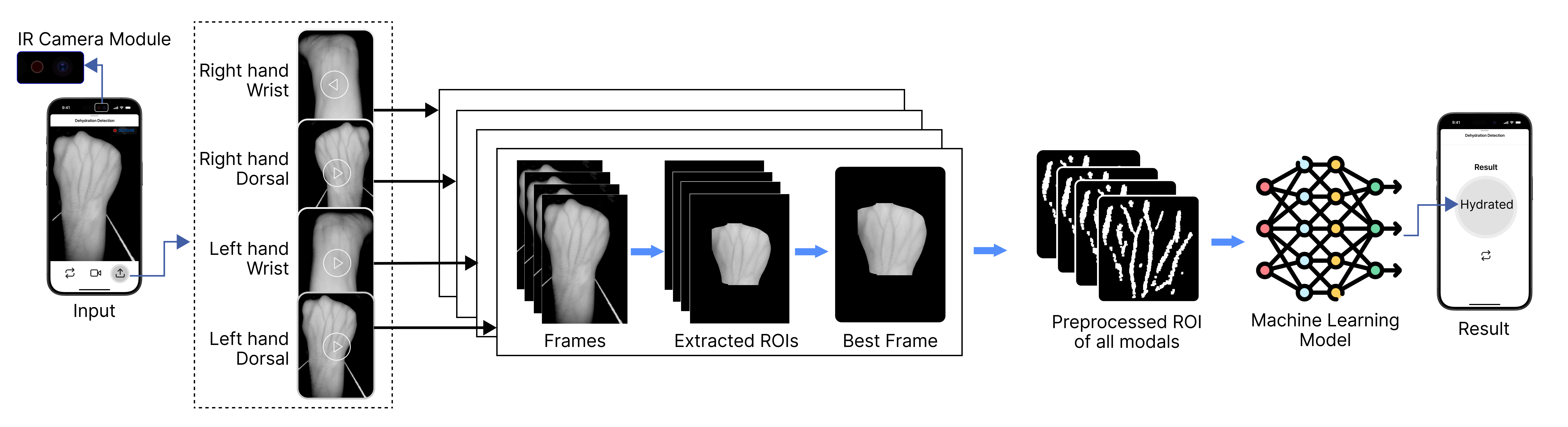 Vein-Based Imaging Approach using Deep Learning for Real-Time Non-Invasive Dehydration Detection
Vein-Based Imaging Approach using Deep Learning for Real-Time Non-Invasive Dehydration Detection On Detecting Malicious Code Injection By Monitoring Multi-level Container Activites
On Detecting Malicious Code Injection By Monitoring Multi-level Container Activites